Signed Pipelines Build Trust in your Software Supply Chain
Trust isn’t given, it’s earned. As the Russian proverb advises, Доверяй, но проверяй — or as U.S. President Ronald Reagan liked to repeat, “Trust, but verify.”
We designed JFrog Pipelines to securely support a large number of teams, applications, users and thousands of pipelines. The latest release brings an industry-first verification capability to Pipelines that protects the authenticity of your binaries, enabling worry-free releases and updates that meet the needs of the most demanding enterprises.
Your SDLC Exposes Many Points of Vulnerability
Accelerating releases through DevOps automation relies on the ability to trust the product of your builds. But your software delivery lifecycle (SDLC) potentially exposes many points of vulnerability. If you’re promoting a build, or deploying to production, how do you know whether the artifact you’re promoting or deploying is legitimate? There’s always a chance that the version of an artifact your pipeline run is expecting to deploy was overwritten by somebody or by another pipeline. Worse yet, what if hackers gain access and compromise the authenticity of your code by tampering with your binaries?
According to a research report sponsored by IBM, the average cost of a data breach was $3.8 million in 2020. We’ve all heard of the high profile attacks (Equifax, Solarwinds, and now Colonial Pipeline), the known attacks number in the hundreds. The SolarWinds breach put the spotlight on how the software supply chain itself is a major attack vector. Bad actors have ‘shifted left’ with their attack target, significantly increasing the blast radius of their attacks. Preventing security breaches during your SDLC is now an expectation from the end users of your software.
The recent Colonial Pipeline cyberattack provided an example of a new front for our battle against cyberattackers. The combination of different types of attack vectors and the number and types of target IT devices gives bad actors a substantial attack surface within which they can operate.
Ensuring the Authenticity of Your Artifacts
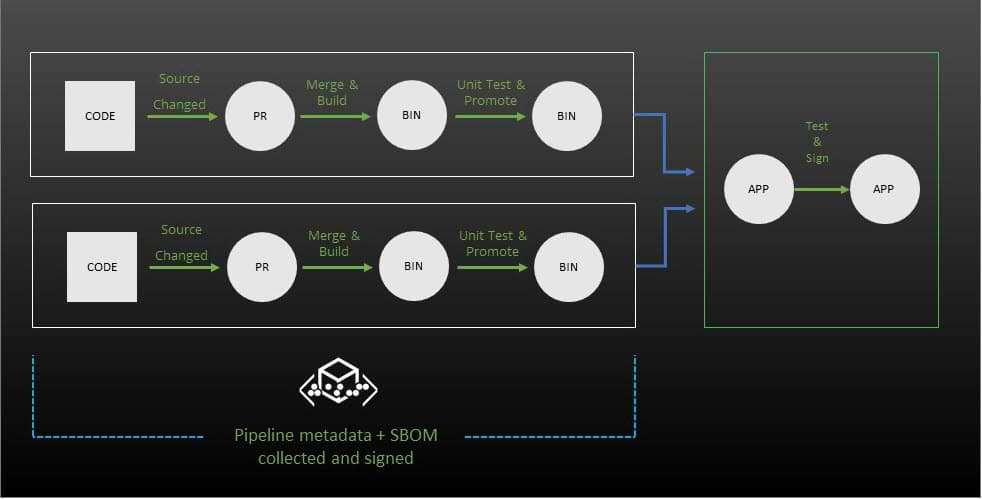
Signed pipelines create trust in the binaries that progress through your SDLC by building a cryptographically signed journal that can validate the authenticity of every artifact generated by your pipeline. With this protected record, developers and operators can ensure that the builds created by a pipeline don’t contain compromised artifacts that have been rewritten by other processes or actions.
More Metadata: PipeInfo
Metadata is a key principle of successful DevOps through the JFrog Platform. The BuildInfo metadata of Artifactory provides traceability of all of the builds you produce.
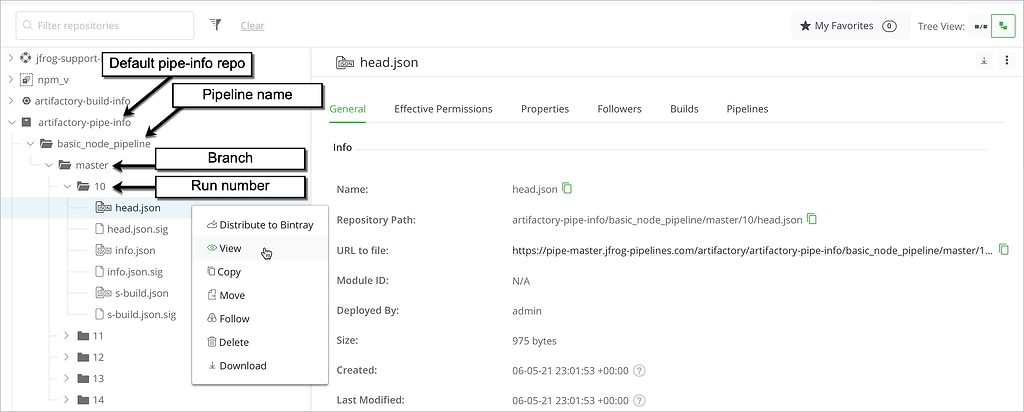
Signed pipelines record an additional set of metadata, called PipeInfo, that connects every artifact produced by a pipeline to the step and run that created it. This comprehensive PipeInfo metadata, readable as a JSON file, provides a detailed, verifiable software bill of materials (SBOM) for every build that enables you to audit your entire software delivery supply chain.
PipeInfo is collected in an Artifactory repository, and identifies the pipelines that generated each artifact, all the different steps that were used as part of each pipeline including their inputs, outputs and configurations, the git commit that triggered the pipeline, and much more. You can access this information programmatically or visually via the UI.
The collected metadata is cryptographically signed while the pipeline is executing and it is associated with the artifacts that are generated as a result of the pipeline. Pipelines can detect the authenticity and ensure the immutability of software as it progresses through the SDLC and block promotion, release bundle creation, or deployments if authenticity can’t be verified.
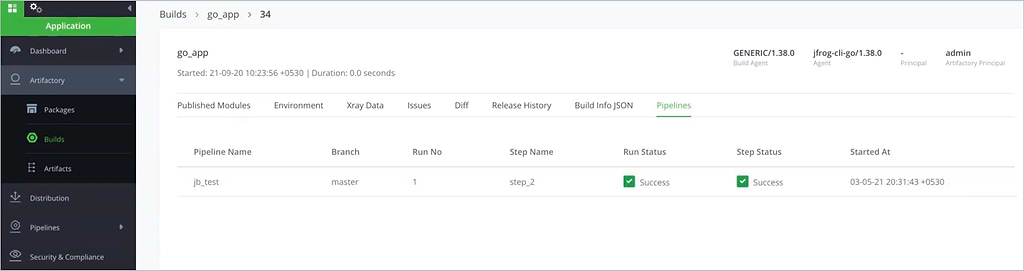
Trace Builds to Steps
With PipeInfo, every build in Artifactory can be traced back to the Pipelines step — and therefore the commands that were run — that produced it. This can be seen in the UI, through a new Pipelines tab in the Artifacts Browser of Artifactory.
From this view of the build, you can click to show the full PipeInfo, or to view the step’s run log in Pipelines.
Catch Up with Industry-First Announcements at SwampUP
Signed pipelines is one of several industry-first capabilities announced at our swampUp DevOps Conference that enable binary lifecycle management at scale. This short summary is a good way to get an overview.
These innovations all contribute to the JFrog Platform difference that can only be gained from a natively integrated set of services working together for comprehensive DevOps and security.
Trust requires verification. “You repeat that at every meeting,” Soviet Premier Gorbachev responded. We’ll be reminding you of it, too.